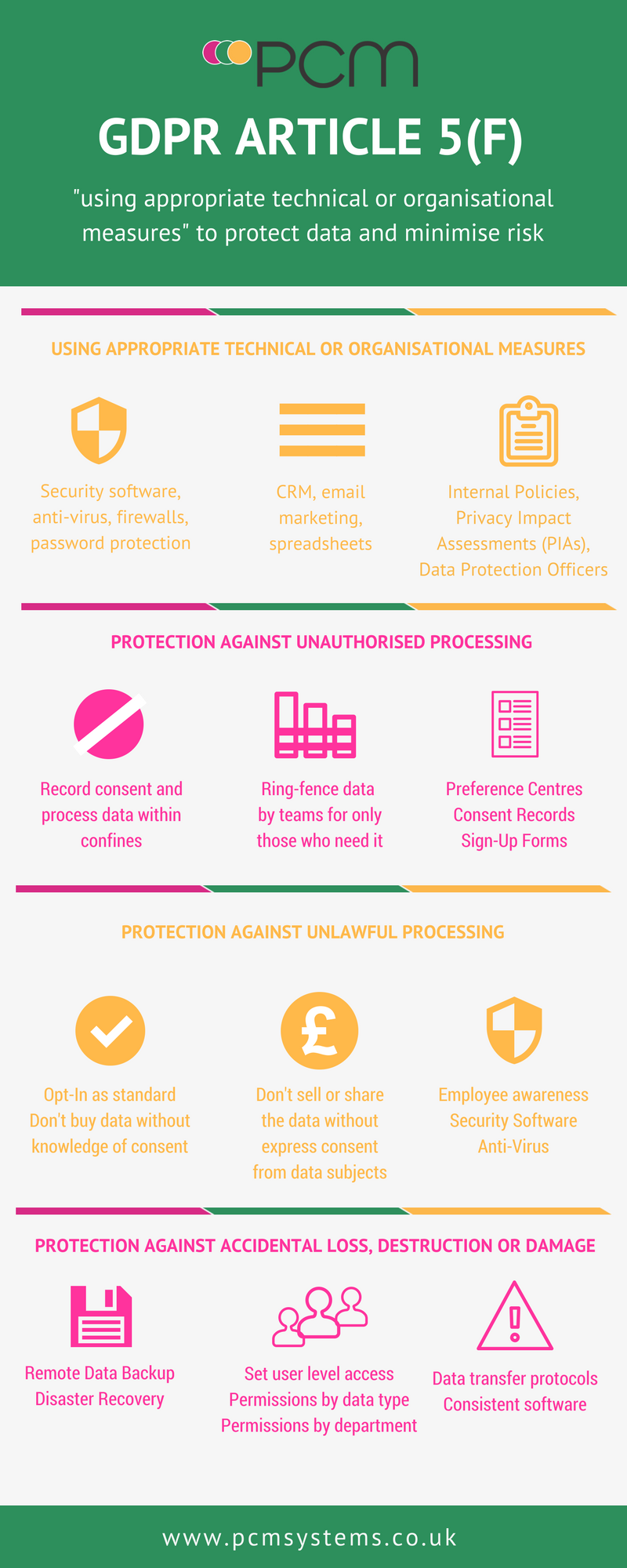
There’s a lot of confusion around GDPR. But there is one point in the Principles of the General Data Protection Regulation that is crystal clear. You must process personal data in a secure manner, and protect that data against loss, theft or damage through organisational processes and appropriate technology.
This is covered in Article 5, Paragraph F of the GDPR text:
“f) processed in a manner that ensures appropriate security of the personal data, including protection against unauthorised or unlawful processing and against accidental loss, destruction or damage, using appropriate technical or organisational measures.”
We’re going to look at this section of the GDPR more closely to help you figure out how you can protect the data you collect and/or process using technology and business processes.
We’ll start at the end:
“Using appropriate technical or organisational measures”
Article 5 f requires businesses to implement organisational processes to enforce the security of the data they collect and process. This can include road mapping data to see where it enters and is used within the organisation and completing a risk assessment. In addition, technology can be used to protect the security of the data.
Not only does that include security hardware and software such as anti-virus, but also the technology you use within your organisation such as your Customer Relationship Management (CRM) system, email marketing platform and company website.
So how else can you use technology and processes in order to comply with GDPR Article 5 f?
Protection against unauthorised processing

We can link unauthorised processing to the previous 5 paragraphs within Article 5. Take point C and the text “adequate, relevant and limited to what is necessary”. What that really means is that you shouldn’t collect more data than you actually need in order to fulfill your obligation to your customer. That might be selling them a product or delivering a service. It also means that you shouldn’t apply more processing than you need to.
Limiting the number of people who have access to the data is one way in which you can protect the data. You can use organisational processes to ensure the right teams have the right data to do their jobs. Technology can be used to ring fence the data in password protected folders or systems.
Using a preference centre or permission form within your CRM or marketing software can also ensure that you don’t process data outside of the permissions the data subject has given.
Protection against unlawful processing

Unlawful processing through data theft is something that data controllers and processors need to take measures to prevent. Without putting adequate data security measures in place you could be liable for data theft or misuse by cyber criminals. Using anti-virus, malware scans and security software can help to prevent common and known cyber security threats.
Unlawful processing would cover using the data in a way that contradicted the consent the data subject had given you. For example, if you had collected the data as part of a transaction, and the customer has not specifically and clearly consented to receiving ongoing marketing phone calls, you cannot then use the data to make marketing (and sales) phone calls. Remember, this applies to consumers and to sole traders. You could still call someone working within a limited company under the label of ‘legitimate interest’.
Other acts of unlawful processing might include selling the data subjects’ information without their express consent or allowing third parties to access the data.
You can use technology to make sure that the data isn’t used unlawfully. Setting up a preference centre for new contacts will help to establish what the data subject does and doesn’t consent to.
For example, you might ask them if they consent to receiving marketing emails, phone calls or SMS. Another option could be consent for their data to be shared with third parties who may market related products or services to them.
There needs to be an opt-in function rather than an opt-out, so don’t pre-fill checkboxes!
Linking your preference centre to your CRM or database will enable you to view the consent for each data subject, and prevent anyone within the organisation from using it unlawfully.
Protection against accidental loss, destruction or damage
Click, click, click and suddenly you’ve lost a database of client data, or accidentally sent it to everyone in your email contacts by mistake.
You can set up rules and processes within your organisation to minimise these risks, but there is always room for human error.
Bolstering your policies with the support of technology can help to minimise the risk of human error causing accidental loss, destruction or damage to the data you collect and process.
Here are some ways you can use technology to support your processes:
-
Set user level access and permissions
- When it comes to your data, documents and folders on your network, you can set permissions for individual employees, teams, departments and seniority levels. For example, you might remove the permanent delete function from junior staff so that they cannot accidentally delete important data. Sharing, reading and editing can also be controlled in this way.
-
Use Remote Data Backup to prevent permanent loss of data
- If a database is accidentally deleted or damaged, having a recent backup is the solution. You can use remote data backup to take a copy of your data at regular intervals so that your restored data is accurate, and not days or weeks old.
-
Adopt consistent data transfer protocols
- If you need to share data internally and/or externally, you should ensure that you have a process in place. It should include the method of transfer, for example via email, a third party service such as WeTransfer or directly sharing access to documents. Do you need to encrypt the data, or add password protection before someone else can access the contents? You could include sensitivity levels such as ‘Classified’, ‘Internal Use Only’ and ‘Open’ so people know which process to follow if you have different transfer processes.
-
Install common software solutions across your entire team
- Data can be damaged if it is passed between different software and programs. To minimise the risk of damage to the data you collect or process, using consistent software across your organisation can help. Does everyone use Microsoft Office or Google’s G Suite, Adobe PDF or a different PDF viewer?
We hope that this blog post has helped you to plan how you will use technology and processes to comply with GDPR Article 5 Paragraph F. Contact us if you would like to review your technology before GDPR is enforced in May 2018.
Date published: 06/03/2018